In this post we create Geo-Replicated Azure Container Registry (ACR) with Premium Tier using Bicep templates.
Azure Container Registry (ACR) is a Platform as a Service product for storing and managing private Docker container images. Azure container registries can include both Windows and Linux images. Typical architecture scanario for ACR usage is to simplify the deployment and management of microservices-based architecture.
Geo-replication - network-close approach
Good practice is to keep a container registry near the data center where images are managed and run. For globally distributed Docker image based applications Azure Container Registry’s Geo-replication enables serving multiple regions with multi-master regional registries:
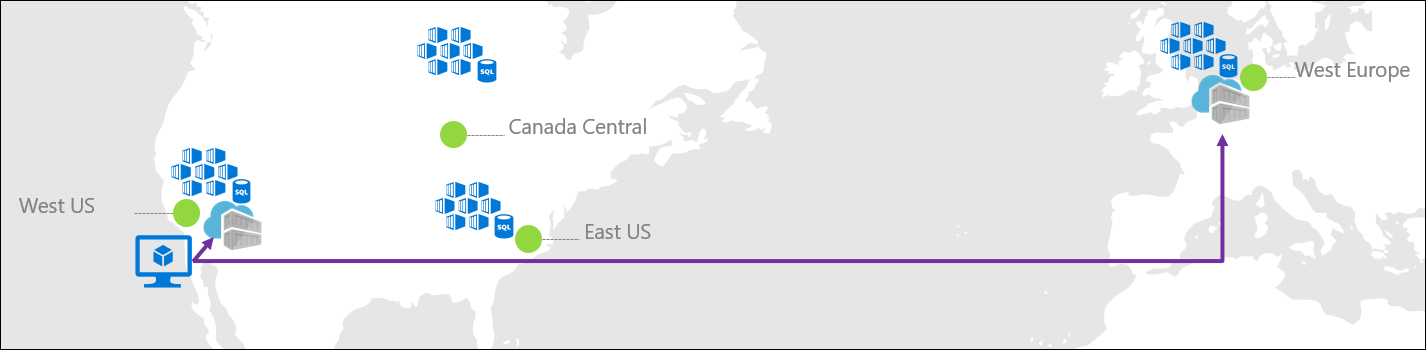
- Single registry, image, and tag names can be used across multiple regions.
- Network-close registry access.
- Single management of a registry across multiple regions.
- Registry resilience if a regional outage occurs.
Review registries.bicep Template
This Bicep template creates a Microsoft.ContainerRegistry/registries resource and sub-resource Microsoft.ContainerRegistry/registries/replications for Geo-Replication.
By default pricing tier is Basic tier resource instance but since we are doing Geo-Replication we need Premiumtier. Hence, we will override the skuName parameter during deployment.
💡 TIP
If you dont’ need Geo-Replication use default
skuNameparameter. That will create aBasictier registry, which is a cost-optimized option for developers learning about Azure Container Registry. Choose other tiers for increased storage and image throughput, and capabilities such as connection using a private endpoint. For details on available service tiers (SKUs), see Container registry service tiers.
This template uses Bicep’s outside parent resource syntax to reference parent of replication resource. I find this a really handy way to build up correct resource naming syntax for child resources: Specify the parent property on the child with the value set to the symbolic name of the parent. With this syntax you still need to declare the full resource type, but the name of the child resource is only the name of the child.
// Resource names may contain alpha numeric characters only and must be between 5 and 50 characters.
param acrName string = replace(replace(resourceGroup().name, 'rg-', 'acr'), '-', '')
param location string = resourceGroup().location
@allowed([
'Basic'
'Classic'
'Premium'
'Standard'
])
param skuName string = 'Basic'
param deployReplication bool = false
param replicationLocation string = 'northeurope'
param replicationName string = 'northeurope'
// Create Azure Container Registry resource
resource registry 'Microsoft.ContainerRegistry/registries@2021-06-01-preview' = {
name: acrName
location: location
sku: {
name: skuName
}
properties: {
adminUserEnabled: false
}
}
// Deploy replication resource conditionally
resource replication 'Microsoft.ContainerRegistry/registries/replications@2021-06-01-preview' = if (deployReplication) {
parent: registry
name: replicationName
location: replicationLocation
properties: {
zoneRedundancy: 'Disabled' // Zone redundancy is still on preview
}
}
output name string = registry.name
output id string = registry.id
Notice that template uses boolean parameter and conditional deployment logic if (deployReplication) to deploy replication to northeurope location.
🚩 NOTE -
adminUserEnabled: falseThe admin account is designed for a single user to access the registry, mainly for testing purposes. Disable admin user for production usage and do not share admin account credentials among multiple users.
Deploy the template to Azure
To deploy Bicep template to Azure, you need to sign-in to your Azure account using Azure command line interface (AZ CLI).
🚩 NOTE
Remember to sign in with your Azure AD account that has Contributor access role to your Azure API management environment.
- Open a Visual Studio Code terminal window by selecting Terminal > New Terminal. The window usually opens at the bottom of the screen.}
- Switch your terminal to the directory where you saved
registry.biceptemplate.
Sign in to Azure with Azure CLI
In the Visual Studio Code terminal, sign in to Azure by running the following command:
az login
In the browser that opens, sign in to your Azure account.
The Visual Studio Code terminal displays a list of the subscriptions associated with this account.
Set the subscription context for all of the Azure CLI commands that you run in this session.
az account set --subscription "your-subscription-name"
Create resource group with Azure CLI
Create a new Azure resource group for your Azure development environment.
az group create --location westeurope --name "rg-yourgroup-we-dev"
Deploy registries.bicep template to Azure
Run the following command from the terminal in Visual Studio Code to deploy the Bicep template to Azure.
az deployment group create --template-file .\registries.bicep --resource-group "rg-yourgroup-we-dev" --parameters skuName="Premium" deployReplication=true
In the example above we are deploying template that creates premium tier Azure Container Registry resource with Geo-Replication location to development environment.
Review deployed resources
Use the Azure portal or a tool such as the Azure CLI to review the properties of the container registry.
- In the portal, search for Container Registries, and select the container registry you created.
-
On the Overview page, note the Login server of the registry. Use this URI when you use Docker to tag and push images to your registry.
 .
. - Select the ACR that you created.
-
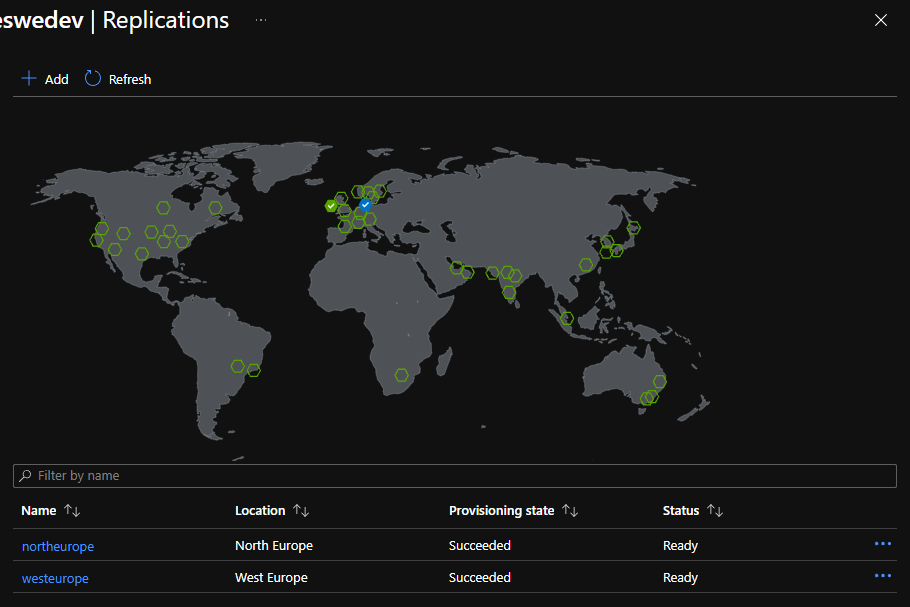
Under Services select Replications and you should see something similar than below where West Europe data center has blue icon and North Europe has green icon.
AZ-CLI - az acr show
Get the details of an Azure Container Registry.
az acr show --name "acryourgroupwedev"
Log in to registry with Azure CLI and Docker CLI
Ensure that you can log in to the registry instance. Specify only the registry resource name when logging in with the Azure CLI. Don’t use the fully qualified login server name.
Azure CLI - az acr login
If you have Docker installed and running you can try following command to login.
az acr login --name "acryourgroupwedev"
The command returns Login Succeeded once completed.
If you don’t have Docker installed or it’s not running you can verify that you can get access token with command:
az acr login --name "acryourgroupwedev" --expose-token
--expose-token switch exposes an access token instead of logging in through the Docker CLI.
See also
- Docker docs: Docker overview.
- Azure Container Registry roadmap.
- Azure Updates related to Container Registry.
- Microsoft blogs tagger with Azure Container Registry.