Preparing to AZ-303
Topics to cover for exam AZ-303 Microsoft Azure Architect Technologies
Microsoft checks following areas in the exam.
- Implement and monitor an Azure infrastructure (50-55%)
- Implement management and security solutions (25-30%)
- Implement solutions for apps (10-15%)
- Implement and manage data platforms (10-15%)
Percentages are the relative weighting of the subject area in the exam. It seems that the emphasis is heavily on Azure infrastructure.
Detailed list can be found in this pdf report.
🎯 Prepare for topic: Implement and monitor an Azure infrastructure
Azure Infrastructure related Microsoft Learn learning paths:
Architect network infrastructure in Azure: 12 modules to learn architect a secure, flexible, network infrastructure in Azure and connect on-premises networks to Azure resources. Before starting the learning path you should be familiar with network concepts such as: VPN, IP addressing and routing. A good book (pdf) to learn these concepts is Azure Networking Cookbook by Mustafa Toroman.
Azure documentation related to Implement and monitor and Azure infrastructure topics is covered in more details below.
Implement cloud infrastructure monitoring
- monitor security
- monitor performance
- monitor health and availability
- monitor cost
- configure advanced logging
- initiate automated responses by using Action Groups
- configure and manage advanced alerts
Implement storage accounts
- select storage account options based on a use case
- configure Azure Files and Azure Blob storage
- configure network access to the storage account
- implement Shared Access Signatures and access policies
- implement Azure AD authentication for storage
- manage access keys
- implement Azure storage replication
- implement Azure storage account failover
Implement VMs for Windows and Linux
- configure high availability
- configure storage for VMs
- select virtual machine size
- implement Azure Dedicated Hosts
- deploy and configure Virtual Machine Scale Sets
- configure Azure Disk Encryption
Automate deployment and configuration of resources
- save a deployment as an Azure Resource Manager template
- modify Azure Resource Manager template (JSON and Bicep)
- evaluate location of new resources
- configure a VHD image
- deploy from an image
- manage an image library
- create and execute an Azure Automation runbook
🎯 Implement virtual networking
Learn about subnetworks:
- https://www.techtarget.com/searchnetworking/definition/subnet
- https://en.wikipedia.org/wiki/Subnetwork
Related Azure services
✔ Implement VNet to VNet connections
Connecting a virtual network to another virtual network (VNet-to-VNet) is similar to connecting a VNet to an on-premises site location. Both connectivity types use a VPN gateway to provide a secure tunnel using IPsec/IKE.

✔ Azure VPN gateways
A VPN gateway is a specific type of virtual network gateway that is used to send encrypted traffic between networks over the public Internet.
- The VNet gateway uses specific subnet called the gateway subnet.
- Each VNet can have two VNet gateways; one VPN gateway and one ExpressRoute gateway.
- VNet can have only one VPN gateway.
- VPN gateway supports multiple connections.
- Gateway SKU defines what kind of workloads, throughputs, features, and SLAs are supported. Use Virtual WAN for more than 30 S2S VPN tunnels.
- Basic VPN Gateway supports max. 10 S2S or Vnet-to-Vnet tunnels and it should only be used for Dev/Test workloads.
- VpnGW1/Az, VpnGW2/Az and VpnGW3/Az SKU supports max 30 tunnels. There are two VPN types: PolicyBased and RouteBased. PolicyBased is supported only with Basic gateway SKU. PolicyBased VPNs supports only S2S connections, and only for certain configurations. Most VPN Gateway configurations require a RouteBased VPN.
PolicyBased VPN
- Supports only IKEv1 which is deprecating.
- Uses static routing.
- Used usually for compatibility with legacy on-premises VPN devices.
RouteBased VPN
- Supports IKEv2.
- Uses any-to-any (wildcard) traffic selectors.
- Can use dynamic routing protocols.
Use RouteBased VPN type for:
- Connections between virtual networks.
- Point-to-site connections.
- Multisite connections.
- Coexistence with an Azure ExpressRoute gateway.
High availability for VPN Gateways
- By default, VPN gateways are deployed as two instances in an active/standby configuration.
-
It is also possible to configure active/active VPN gateways for VPN SKU higher than Basic/Standard.
-
VPN gateway could be configured also as a failover for ExpressRoute based connections.
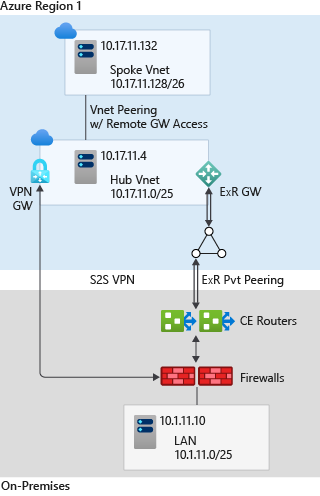
- Zone-redundant gateways can be configured to protect on-premises network connectivity to Azure from zone-level failures.
VPN gateway connectivity scenarios
-
Connect Azure VNet to other Azure VNet through a network-to-network connection.
-
Connect on-premise to Azure VNet through a site-to-site (S2S) VPN connection between two endpoints that are located on the public Internet. Site-to-site VPN connection is terminated by a VPN device on the on-premises network and an Azure VPN gateway on the Azure virtual network. VPN device in local network is configured with a shared key and public IP address of VNet gateway.
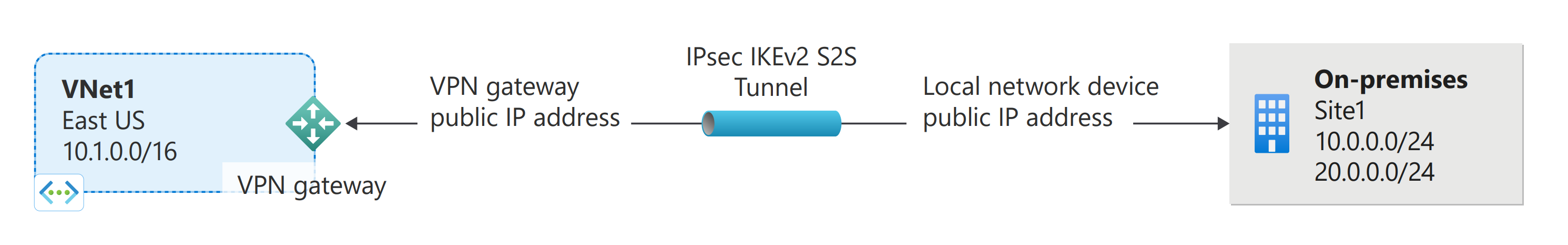 .
. -
Connect individual devices to Azure VNet through a point-to-site (P2S) connection. P2S connection requires a RouteBased VPN type.
Learn more
- Microsoft Learn Modules:
-
Connect your on-premises network to Azure with VPN Gateway. This module contains exercise that configures Site-to-Site VPN connection with simulated on-premise network using az-cli and Azure cloud shell.
-
- Microsoft docs tutorials:
- Pricing:
✔ Implement VNet peering
You can connect virtual networks to each other with virtual network peering. Once virtual networks are peered, resources in both virtual networks can communicate with each other using private IP addresses.
Connectivity scenarios that VNet peering supports:
- VNets in different Azure regions for example between VNet1 in Nort Europe data center and VNet2 in West Europe datacenter.
- VNets in two different subsriptions.
- VNets in two different Azure AD tenants.
🚩 NOTE
to connect the networks by using virtual network peering, you have to create connections in each virtual network - both ways from VNet1 -> VNet2 and VNet2 -> VNet1. To maintain VNet peering configurations user needs at least
Network ContributorRBAC role on the VNet.
❌ WARNING
Do not overlapp address spaces. IP address spaces of connected Azure VNets and on-premises must not overlap. This is also true for peered virtual networks. Otherwise there will be pain and crying.
Share on-premise connecitivity between VNets
Transitive connections to on-premise with Azure VPN gateway transit: configure the Allow gateway transit option in the hub VNet with on-premise gateway. Also configure the Use remote gateways option in any spoke virtual networks. See how-to configure VPN gateway transit for virtual network peering with hub-spoke architecture in Azure.

Learn more
- Microsoft Learn modules:
- Microsoft docs tutorials:
Implement Azure Active Directory
- add custom domains
- configure Azure AD Identity Protection
- implement self-service password reset
- implement Conditional Access including MFA
- configure fraud alerts
- configure verification methods
- implement and manage guest accounts
- manage multiple directories
Implement and manage hybrid identities
- install and configure Azure AD Connect
- identity synchronization options
- configure and manage password sync and password writeback
- configure single sign-on
- configure Azure AD Connect cloud sync
- use Azure AD Connect Health
🎯 Prepare for topic: Implement Management and Security Solutions
Manage workloads in Azure
- migrate workloads using Azure Migrate
- implement Azure Backup for Azure workloads
- implement disaster recovery
- implement Azure Automation Update Management
Implement load balancing
Implement network security
Implement Azure Load Balancer
implement an Azure Application Gateway
implement Web Application Firewall
implement Azure Firewall
implement Azure Firewall Manager
implement Azure Front Door
implement Azure Traffic Manager
🎯 Implement Network Security Groups
Related Azure Services
Azure Network Security Group (NSG) is used to filter network traffic to and from Azure resources in an Azure virtual network.
Network security groups are assigned to a network interface of a VM or a subnet.
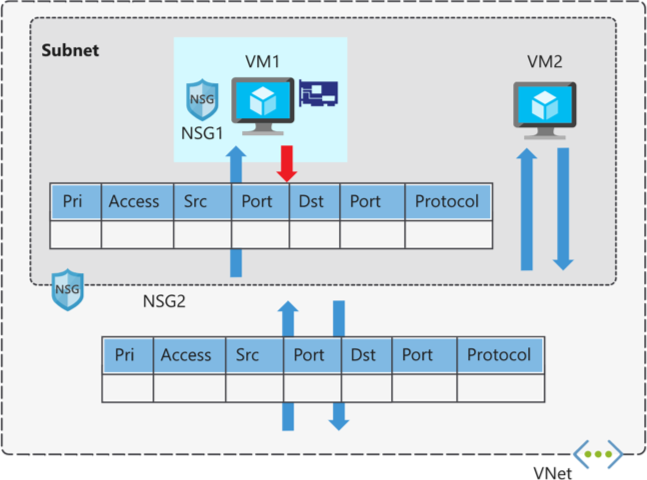
Security Rules
- NSG security rules are evaluated by priority, using the 5-tuple information (source, source port, destination, destination port, and protocol).
- On first rule match further processing stops.
- Rules can allow or deny traffic.
- Augmented rules are used to simplify management of large number of rules.
- Service tags are used to control traffic to Azure service type globally or specific region.
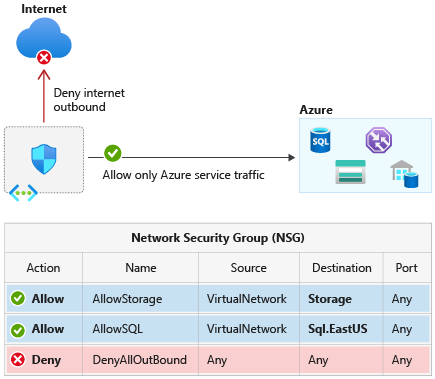
Learn more
- Microsoft Learn module: Secure and isolate access to Azure resources by using network security groups and service endpoints.
Implement Application Security Groups
Related Azure Services
Azure Application Security Group (ASG) allowes grouping of virtual machines and define network security policies based on those groups.
Learn more
implement Bastion
Implement and manage Azure governance solutions
- create and manage hierarchical structure that contains management groups, subscriptions and resource groups
- assign RBAC roles
- create a custom RBAC role
- configure access to Azure resources by assigning roles
- configure management access to Azure
- interpret effective permissions
- set up and perform an access review
- implement and configure Azure Policy
- implement and configure Azure Blueprints
Manage security for applications
- implement and configure Key Vault
- implement and configure Managed Identities
- register and manage applications in Azure AD
See also
- Pluralsight Certification Prep Path: Microsoft Azure Architect Technologies (AZ-303).
- Microsoft products for Azure Networking.
- Azure Architecture Center



