Understanding and Testing the az ad app credential reset Command in Azure AD
In application development and management, ensuring the security of your application is crucial. One such measure is routinely resetting the credentials for Azure Active Directory (AD) App Registrations. In this post, we’ll delve into the az ad app credential reset command, explore its options, and discuss some best practices regarding credential management.
Prerequisites
Before we dive in, make sure you have the following:
- An active Azure account.
- Azure CLI installed on your machine or as an alternative you can use Azure Cloud Shell.
- At least one Azure AD App Registration for testing purposes.
Process Overview
We’ll be using the Azure CLI to navigate through our Azure resources. Our goal is to understand how the az ad app credential reset command functions, explore its --append option, and differentiate between resetting a credential secret and a certificate.
Understanding the Command
The az ad app credential reset command resets the credentials of an Azure AD App Registration by creating a new password credential (Client Secret).
az ad app credential reset --id <app-registration-client-id>
Testing --append switch
The --append switch, when set, preserves old credentials, which can be useful when you’re rotating secrets and need to avoid downtime. When not set, the command removes all old credentials (Client secrets).
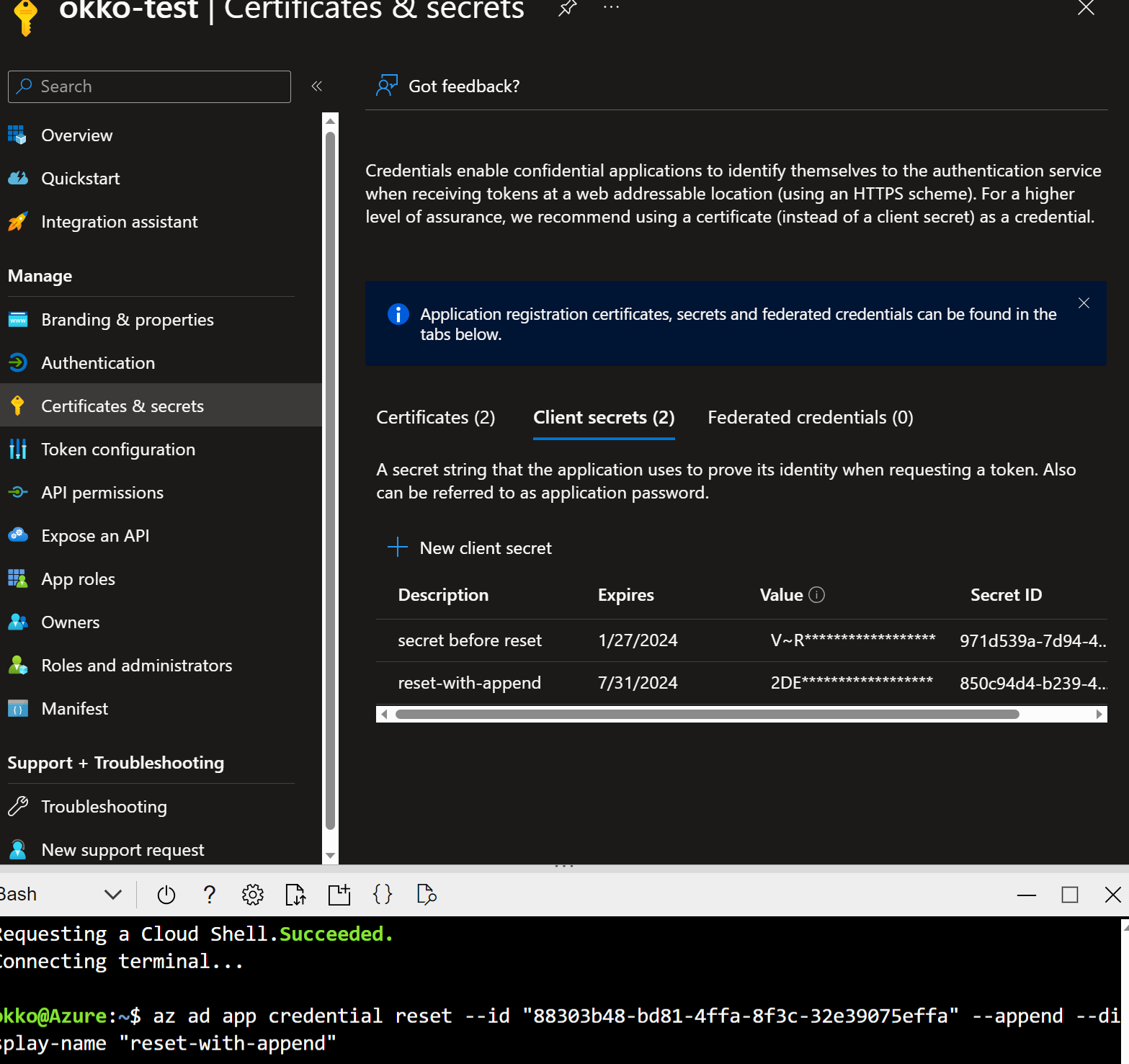
With --append switch
az ad app credential reset --id <app-registration-client-id> --append
This command will preserve all existing credentials.
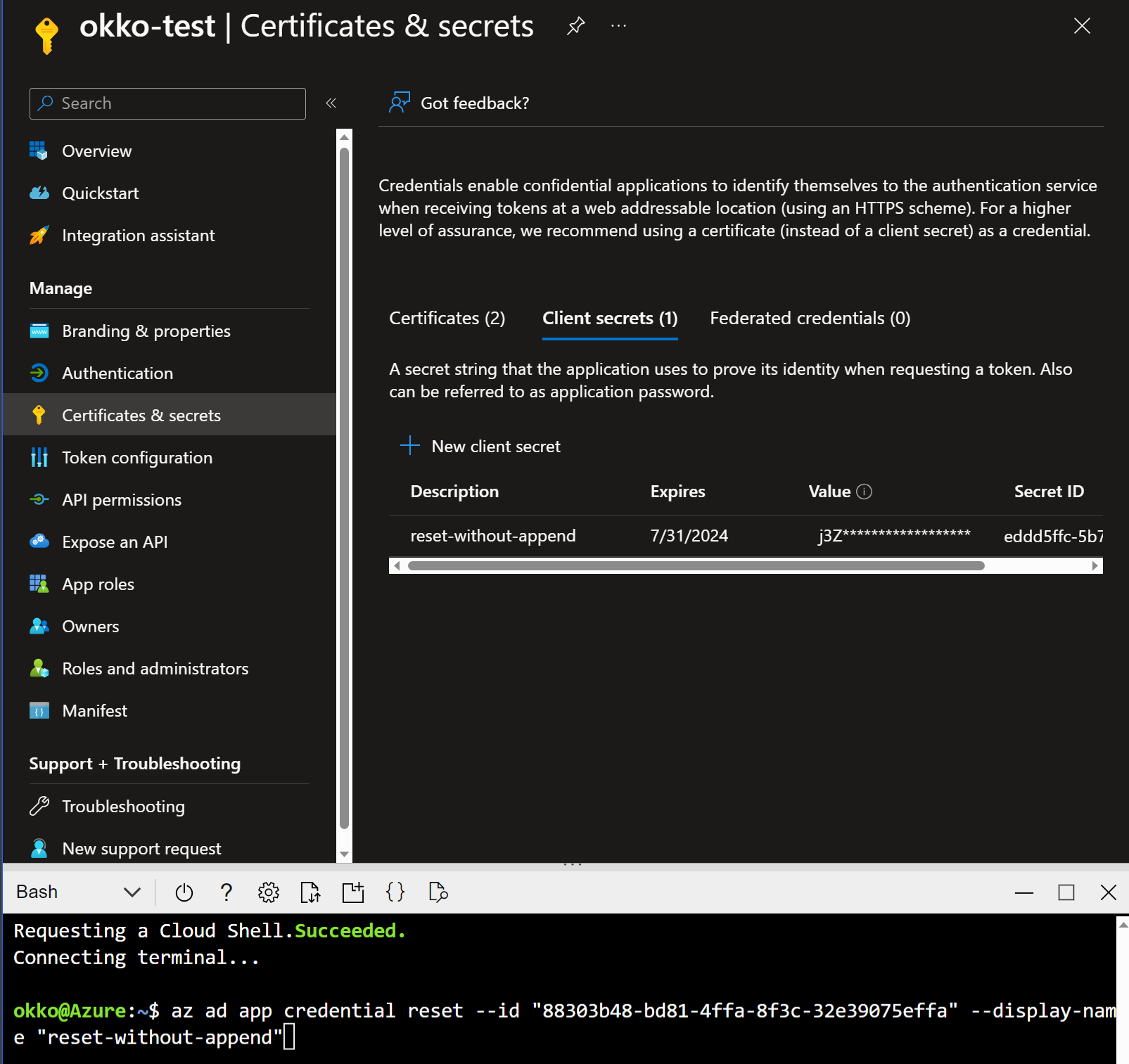
Without --append switch
az ad app credential reset --id <app-registration-client-id>
This command will delete all existing password credentials (Client secrets) and creates a new one. However, it doesn’t remove Certificate credentials.
You can use az ad app credential list --id <app-registration-client-id> to verify the changes in both cases.
🚩 NOTE: you should store the secret value in a secure location. If you lose the secret, you’ll need to reset it again since Azure Portal doesn’t show the secret value later.
Resetting Secret vs. Certificate
By default, the az ad app credential reset command creates a password credential. If you want to create a certificate credential instead, you can use the --cert and --create-cert options.
🚩 DANGER: running the command with
--create-certoption even with--appendoption will delete all Client secrets.
Let’s create a self-registered certificate credential with Azure Cloud Shell – note before running this ☝
az ad app credential reset --id <app-registration-client-id> --create-cert
This will create a self-signed certificate private key file with name similar to tmp12321fa.pemin your home directory and upload the public key to your Azure AD App Registration. Note that any existing Certificate and Client secret credentials will be deleted. If you run the same command many times, it will create a new certificate each time and it will replace the old one in Azure AD App Registration.
Use az ad app credential list --id <app-registration-client-id> --cert to verify the new certificate credential.
az ad app credential reset --id <app-registration-client-id> --create-cert --append
This will create a new certificate credential and preserve the old one. However, it will delete all Client secret credentials.
Good Practices
One Secret per App Registration
Having one secret per app registration is generally recommended for simplicity and ease of management. Especially we considering to implement fully automated secret reset solution. However, there are scenarios where multiple secrets might be needed, such as if the consuming application supports and uses secret rotation. In such cases, make sure each secret is properly tracked and managed.
Secret Rotation
Regularly resetting app credentials is crucial for security. Define process for it and consider implementing an automation to rotate secrets and ensure that old secrets are invalidated.
Using Certificates
For higher security, consider using certificates instead of secrets. Certificates are more secure, harder to compromise, and can be managed more effectively in an enterprise environment.
Conclusion
Understanding the az ad app credential reset command and its options helps in effectively managing Azure AD App Registrations. Regularly resetting these credentials is vital to maintaining the security of your Azure applications. Some of the command’s options, such as --append, can be useful in certain scenarios, but it’s important to understand how they work and their limitations. Also, they are even dangerous if used incorrectly.
- Use
--appendswitch to preserve old credentials when rotating Client secrets. - If you are using both Client secrets and Certificates, you should consider separate storing them to two different app registrations or not use
az app credential resetcommands because the commmand will delete all Client secrets when creating a new certificate credential even with--appendoption. - It is recommended to have one secret per app registration for simplicity and ease of management.
- Define process for secret rotation and consider implementing an automation to rotate secrets and ensure that old secrets are invalidated. secret.